Users of AMD motherboards will no longer suffer from buggy fTPM firmware.
TPMs and fTPMs
Trusted Platform Modules is an concept about decoupling certain security functionality in a separate hardware module that is protected against malicious actors coming either from the operating systems or externally. Here "trusted" means that we trust it more than operating system that can be, for example, infected by a malware implants. So when one says "TPM" he/she usually assume a TPM chip that is mounted on a computer's motherboard. That chip has special kind of protected memory that you cannot extract information from, even if you unsolder it and try to read it by using all super expensive equipment in your electronic lab. This memory is used to securely store sensitive information like private keys (used for cryptographic signing of data) or encryption keys (for symmetric encryption). For instance, when an OS needs to sign data, it initiates a request to the TPM and it generates the signature, while the OS never has access to the contents of the private key - everything happens inside this black box.
But consumers want cheaper and smaller devices, and the industry is constantly trying to fulfill their needs by fighting for every square millimeter on a circuit board and for every cent of final cost. Here come fTPMs, or firmware-based TPMs. Is you might already guessed, this is a software implementation of TPM that does not require a separate chip. No physical space needed, no additional power lines, and easy to upgrade because it's the software in a flash memory. Of course, this fTPM code is executed by CPU in a so-called trusted execution mode, so that other software running on the same CPU cannot access it outside of the predefined set of APIs.
AMD's fTPM
AMD has started to equip their motherboards with fTPM allowing users to have such nice features as Trusted Boot (or Secure Boot), when the authenticity of the operating systems is cryptographically verified by the firmware before it gets booted. The fTPM feature is not must-have and can be enabled or disabled in UEFI setup, like this:
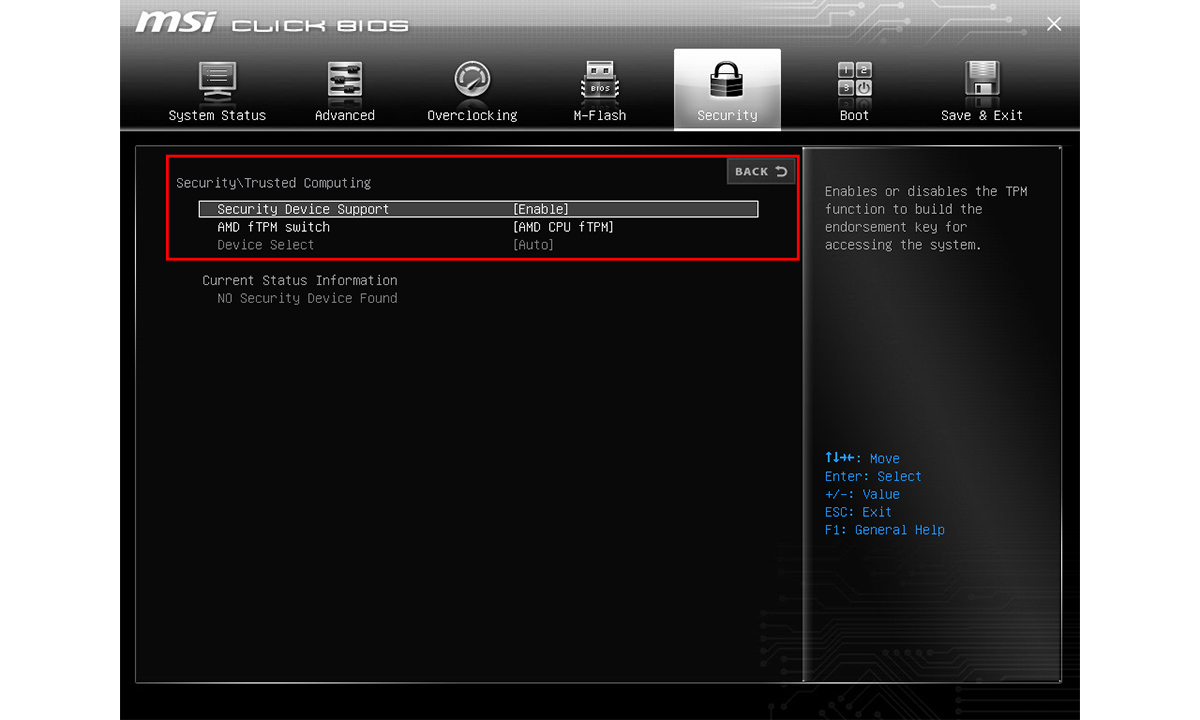
However, as software is written by humans, it is never perfect, and AMD users started massively report stability problems if they enable fTPM. Their computers randomly hang for short periods of time, that is quite annoying especially while playing games or watching movies. For some reason this effect has been called "stuttering". Interestingly, if one search for "AMD fTPM" on the Internet, most of the top links found will describe this stuttering effect and how people workaround it. Luckily, the bug was fixed in further versions of AMD's firware.
Linux Kernel approach
With the evolution of TPMs also evolves its Linux support, allowing other kernel subsystems, as well as user-space programs, to use TPM functions, generating high-quality random data being one of it. If the driver is loaded, a TPM is exposed by the kernel as character device /dev/tpmX. The sysfs place for them is /sys/class/tpm.
From the other hand, the kernel has a concept of hardware random number generator, that is essentially an abstract interface above different ways of getting reliable and unpredictable random numbers, accessible via the /dev/hwrng device. As TPMs can supply "trusted" random numbers to the system, it's no surprise that hwrng uses the fTPM as source of random numbers if it's found on the system, leading system to the above-mentioned "stuttering" effect whenever an fTPM is used by hwrng.
The fix
AMD engineers issued a changeset that instructs hwrng to skip using fTPM if it detects a buggy version of the firmware. In this case the kernel outputs a log message like this:
"AMD fTPM version XXXX causes system stutter; hwrng disabled"
Useful Links
